Cyber security services
Penetration testing
Penetration testing, or pen testing for short, is a simulated cyber attack towards your system. Pen testing measures your cyber defenses and exposes your vulnerabilities, and gives you the information you need to patch them before a real attack takes place.
Targeting your vulnerabilities
A pen test is always tailored to match your vulnerabilities. The ensure this, the scope of the test is agreed with you to provide the best match with your vulnerabilities. The testing setup can vary based on the starting information. The test can be launched with a full or limited set of information on the target system, or with no information at all, depending on what kind of scenario you want to simulate.
How is it done
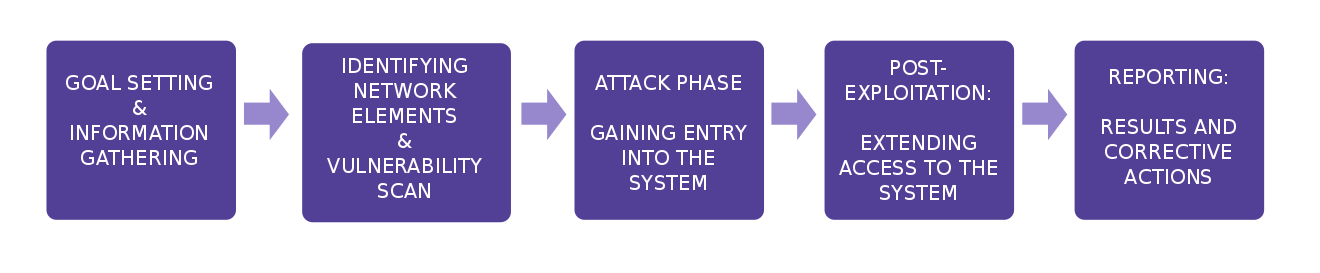
A pen test follows a set procedure.
- Pre-engagement: A meeting to set the scope of the test
- Intelligence gathering: Finding all publicly available information
- Threat modeling: Listing the most important assets and secondary targets providing attack routes to them.
- Vulnerability analysis: Finding routes to the system through port and web scans and configuration bugs.
- Exploitation: The actual attack, to bypass all existing security measures undetected for as long as possible.
- Post exploitation: The attack after the attack, ensuring continued access to the compromised system and entering deeper layers of the target system.
- Reporting: Reporting the key findings of the test and the technical details of the testing procedure.
Understanding the status is the key to improvement
It is not possible to know how good your defenses are unless they have been tested.
The testing scenario that is best for you and your organization depends on the vulnerabilities you have. The options range from DDoS emulation to penetration testing, and include both manual attacks as well as load and attack tests done using our testing tools. The scope of the testing varies, but the result is always increased awareness of risks and protection from cyber threats.