Protecting SCADA from security breaches
Posted onOperational technology is not built for cybersecurity
In 2015, a cyber-attack shut down large parts of the Ukraina power grid. A total of 73MWh of energy was not supplied. This was only a medium breach, but a major one could be just around the corner. While the attacker targeted the power plant on multiple levels, they controlled the plant by seizing control of SCADA, the control system behind operational technology.
A breach in SCADA can cost money, even lives
SCADA is the most common control system. However, it was not built with cybersecurity in mind. In the digital world, SCADA is vulnerable to attacks. Attacking SCADA can mean either introducing minor but malicious tweaks to settings or disabling it entirely. This can lead to defective products and losing customer trust. In the worst case, it may mean that you lose the production assets and lives of people.

React on time
Rugged Tooling has joined ABB’s SynerLeap innovation hub with one goal in mind, to protect people, products, and profits from integrity breaches. We want to help ABB and its partners to secure their critical infrastructure. Rugged Tooling wants to help all industries to be aware of breaches and react to them on time.
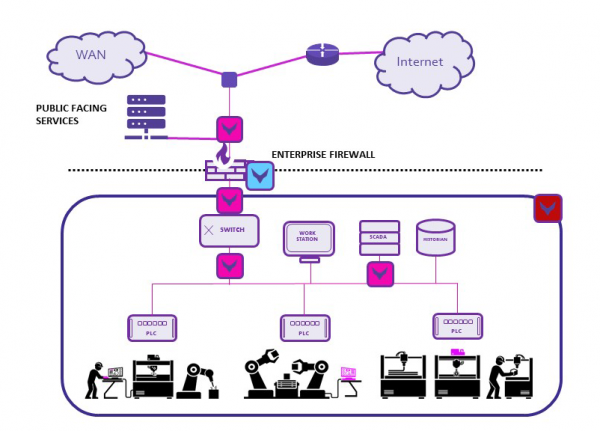
How to secure the operational network
A secure system can mitigate cyber threats and insider risks, can detect device malfunction and unauthorized devices. We provide several building blocks to create such a system.
- First, you need to have complete visibility into the network. Data Monitoring with our Sensor assesses the data from bottom to top layers, following relevant security standards. The system digs into protocols such as Modbus TCP/IP and Profinet to identify the vulnerabilities and threats. The network of sensors makes sure no threats are left in the dark, but they are all reported in real-time.
- We also test the current security systems, such as the firewall, the key asset in a secure network. Testing ensures the firewall and its configurations are set to protect the system to its best ability.
- The security systems must be built on a robust network. Our network emulator tool can make sure the network itself is robust enough by emulating live network conditions in the data.
How to get real-time visibility?
Data sensors monitor traffic in several interfaces in the OT network, where they constantly compare the data to the typical traffic as well as threat feeds. The sensor uncovers malware, device malfunctions, and security threats. The system analyzes the data to get metadata statistics, alerts, log files, and raw packet captures.
Easy access to relevant data provides actionable insight
- Our correlated database lets you drill down on the raw data related to an alert for further investigation.
- The sensor is always up to date due to the self-configuring filter. The filter updates itself constantly based on the alerts and triggers.
- The sensor abilities help to track down and identify the problems. Timeshift feature records data from before an incident, which gives detailed input to forensics.
- To confirm data integrity, we use a blockchain system from GuardTime.
Integrations to support ABB digital transformation
The sensors integrate easily to any platform, SIEM, SOC, or NOC. They provide visibility to the traffic and provide clear insight and relevant data. This is what you need to keep the operational environment securely running and profitable.
With these tools, we aim to support securing ABB critical infrastructure. Our goal is to be part of ABB Digital transformation using both ABB AbilityTM platform and AZURE.
Reach out to us & let’s develop great things together!