Cyber security solutions
Can you handle a DDoS attack?
Emulated DDoS attack
An emulated DDoS attack reveals the level of your cyber resilience. It shows the bottlenecks in your network, your recovery capability and the gaps in your procedures.
A simulated attack is a controlled way of testing how you can handle an attack. You can test where the limits of your actual DDoS protection are and whether your intrusion detection and protection provider keeps its promises. It also allows you to test recovery procedures after an attack has crashed the system. Testing allows you to find the gaps in your protection before you need it.
With our flexible tool Ruge, you can hit your system with enormous amount of malicious traffic.
Our team is available for penetration testing, where they use all their skills in addition to the Ruge tool to thoroughly analyze your defences.
DDoS attack generation
Our tool, Ruge, can generate realistic DDoS attacks, so you can test your defences before deployment.
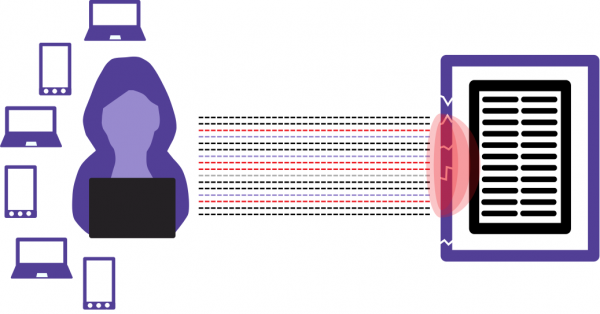
A simulated attack is created by mimicking attack traffic created by millions of attack sources, such as the endpoints in a botnet. It is possible to combine the attack with a typical traffic load, making the attack as real as possible.
Our solution enables tailoring the attack to target your vulnerabilities. You can craft an attack scenario based on your system and your needs, to match any scenario, even those in early stages of development.
Check our case study how we tested the defences on a live network with an emulated attack.
Read more in our blog
How does DDoS emulation work in practice?
A real DDoS attack consists of traffic coming from a vast botnet, all directed at a single target. The emulated attack simulates this by generating a large amount of traffic, comparable to a real attack. This traffic is created to appear to be coming from multiple IPs. To make the scenario even more real, a bottom line typical traffic can be run at the same time as the attacks.
Our IP load generator Ruge is a flexible tool for creating high amounts of network traffic. Here’s how it works:
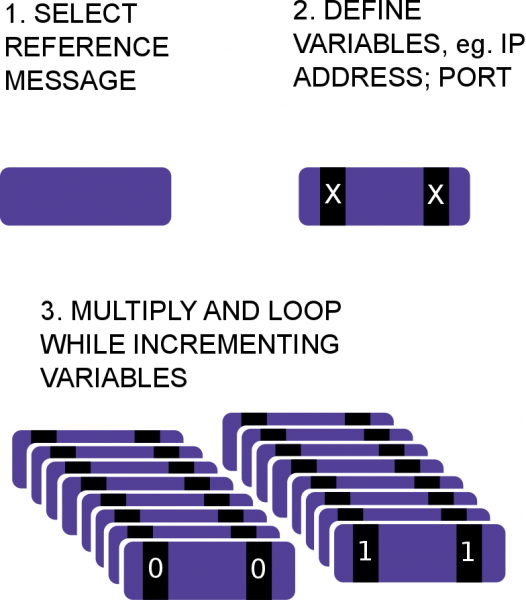
Creating your scenario
You can select any message that is relevant in your system. This allows you to select a specific message even from a system that is still under development.
In a real attack, the messages come from a number of sources and vary in many ways. Defining the variables allows you to emulate a wide range of sources and message contents.
By multiplying the messages while incrementing the variables, an attack with variable content is created. The attack can be controlled in detail to get detailed and repeatable results that enable focused action.
Creating an attack from the library
The tool used in our solution is our powerful Rugged IP load generator Ruge. It provides you with the options of either selecting the attacks from a library or crafting the scenarios yourself. Our library includes a wide range of attacks, including specifically targeted attacks for base stations and VoIP.
The attack library includes for example these typical attacks:
- TCP SYN flood attacks
- UDP flood attacks
- DNS flood attacks
- Ping of Death
- Ping flood
- Smurf attack
- ARP flood attacks
- Teardrop attacks
- TCP sequence prediction attack
- Attacks with malformed or fragmented packets
- TCP port scan attacks
- etc.
The benefits of DDoS emulation
A controlled, defined attack allows the test engineer to see what happens within the network with each stage of the attack.
Alerts and rerouting can be monitored and the effectivity of your DDoS mitigation system can be tested.
Deliberately crashing the target system enables testing the recovery processes and systems.