What are DDoS attacks?
Posted onDDoS stands for Distributed Denial-of-Service attack. The attack is distributed over a large network of compromised endpoints, computers or other devices with an IP connection. This large network is called a botnet, which resembles an army under the command of the attacker. Unlike a real army, however, the endpoints are compromised and used as part of the botnet unknown to their owners.
The goal of the attack is to cause a denial of service for the users of the target system. This is accomplished by prompting each of the members in the botnet to start sending messages to the same target at the same time. This flood of incoming messages is intended to deplete the target resources to case the system to slow down or crash entirely, and to deny the service from its users.
How are the DDoS attacks created?
The hacker starts to build the botnet by exploiting a vulnerability in a computer, called the DDoS master, to infect it with malware. The DDoS master then starts to spread the malware, infecting other vulnerable devices to make them join the botnet. The devices in the botnet are often called zombies or bots.
Each infected device spreads the malware further, gathering more and more devices to the botnet. The number of devices in a botnet can be extremely high with no known upper limit. Once the attacker is ready to launch the attack, the amount of attack traffic from the botnet has been known to exceed 1 Tbps.
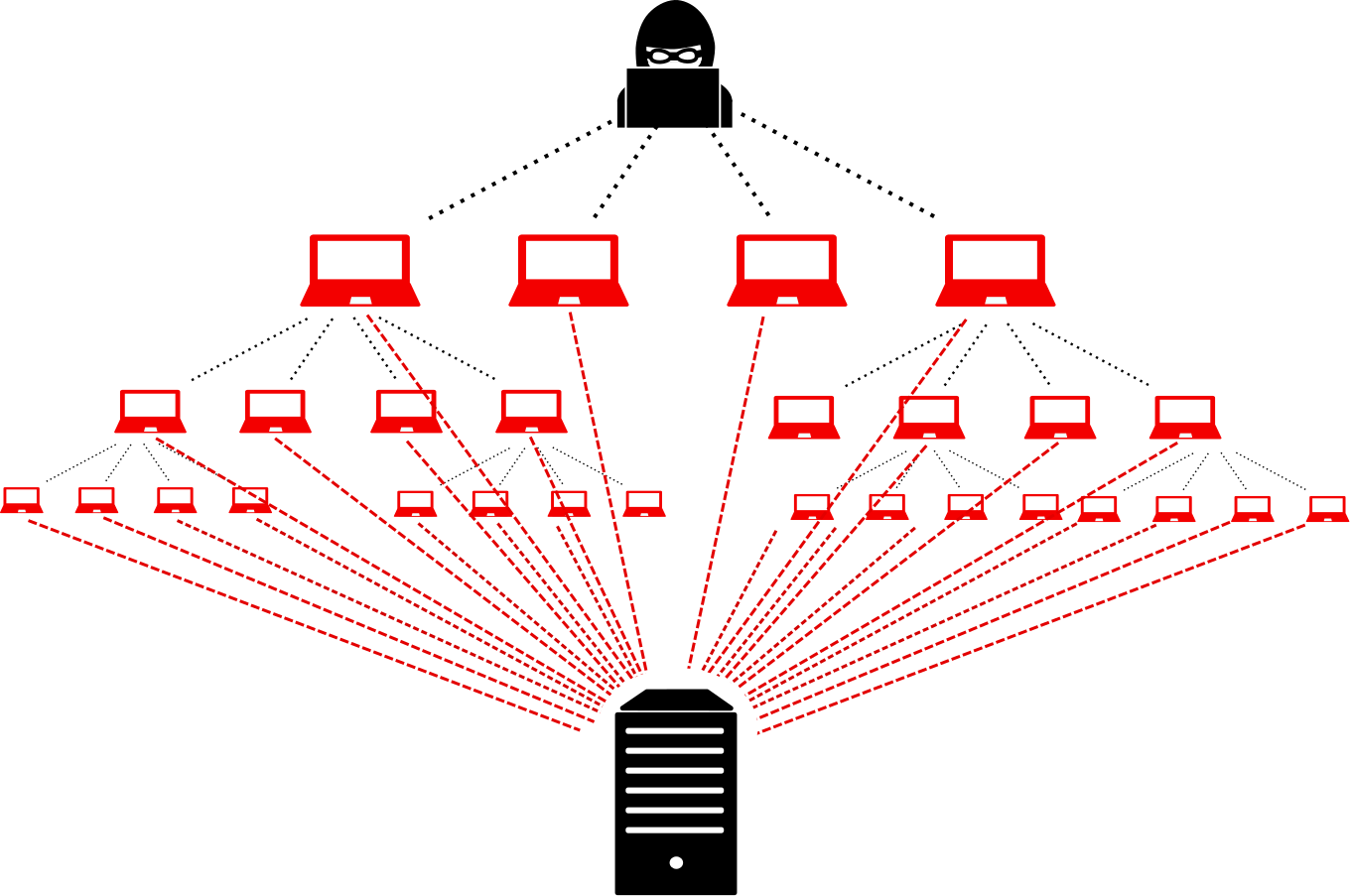
The devices in the botnet may be unpatched computers, but recently, IoT devices have been the source of the heaviest attacks. The security measures of many connected devices are often poor. The devices often come with default login credentials that are difficult or even impossible to update, leaving the devices vulnerable for exploitation.
What happens during a DDoS attack?
This depends on the type of the attack. There are different types of DDoS attacks:
Volumetric attacks
create a packet flood towards the target system in an attempt to use up all available bandwidth and block out the legitimate traffic. The service interruption is created through either overloading the server capacity, or overloading the ability of the server to handle and respond to the overflowing traffic.
Example of a volumetric attack: UDP CharGEN flood
In a UDP flood attack, the attacker sends a large number of UDP packets from various sources to single target. The packets themselves might be targeted to a large variety of ports, or targeted at a specific port. One example is the CharGEN flood, where the attack is targeted at port 19, used for the CharGEN protocol. When the target attempts to process all of these requests, the number of the requests will be too much to process. The server resources will eventually be exhausted, knocking it offline or forcing a reboot.
Protocol attacks
aim to deplete the target resources by sending requests that need a response from the target system, such as SYN flood or Ping of Death attacks or consuming the system resources through sending in fragmented packets that the target system will try to reassemble.
Example of a protocol attack: SYN flood
In an SYN flood, the attacker sends a huge amount of TCP SYN packets from several source ports to an open destination port in the target but does not continue TCP connection establishment further. The client initiates a new session with the SYN packet, and the system expects the host to assign and check the session until the client closes the session. In an SYN attack, the connections are left open. The open connections exhaust the server connection table memory, making it incapable of processing any legitimate requests.
Example of a protocol attack: Ping of death
In a Ping of death attack, the attacker sends ICMP Echo Requests bigger than 65535 bytes from several addresses to target. A packet is fragmented according to specification, but due to the excessive size, the result may be a buffer overflow and system crash, which are then used to breach the network for example for malware injection.
Application layer attacks
aim to crash the web server. They are typically very slow and difficult to set apart from usual user traffic, that is until they consume all of the target system resources. Application layer attacks typically target DNS, HTTP, and HTTPS protocols.