Securing the telco environment
Posted onTesting resilience and ensuring recovery
The number of cyberattacks is endlessly growing, also against VoIP calls. To help our customers verify their resilience against such attacks in LTE and IMS networks, we’ve added support for the SIP protocol in Rude. This gives you a simple way to set up attack scenarios utilizing the SIP protocol to ensure that your security measures can detect and prevent the attacks.
The cyber attacker who is targeting SIP will be one with a lot of knowledge and background information already, and thus the attacks would have serious consequences if successful. To secure customer data, it is vital to ensure the service and network are resilient to attacks before they are deployment.
Types of security attacks
Tapping a voice call
The attack targets the authorization of the call. If the attacker is able to get in as a Man-In-The-Middle, they could change the authentication scheme to access the call authentication keys and ciphering algorithms. This is not a small deal as the keys would then enable the hacker to tap a phone call.
Diverting a call
Using the same Man-In-The-Middle approach, the attacker might also go for falsifying the header fields in the SIP to even change the call ID or the call TO or FROM fields to divert it somewhere it was not intended. Both this and the first are examples of protocol attacks that would have devastating consequences if critical information was discussed in those calls.
As cyber attacks have become a part of daily life, the cyber security resourcing is moving focus from protection to resilience. The new feature allows the user test it, by building such scenarios easily, to test the detection and response procedures of their system.
Negative testing / Recovery testing
An attacker might also try to cause a denial of service by sending in unordered message sequences or incorrect flows. Also such incorrect messages might be due to a system error. Regardless of the root cause, abnormal and random inputs to the system may cause overload of system resources and eventually system crash, a network operator’s worst nightmare. By creating the situation using the modification helps to ensure a quick and smooth recovery in the real situation.
Creating the attack
attributes can be changed in the header fields, as shown in the picture, to replicate any of these possible attacks or several other protocol attacks. This feature gives you the tools you need to test the system resilience.
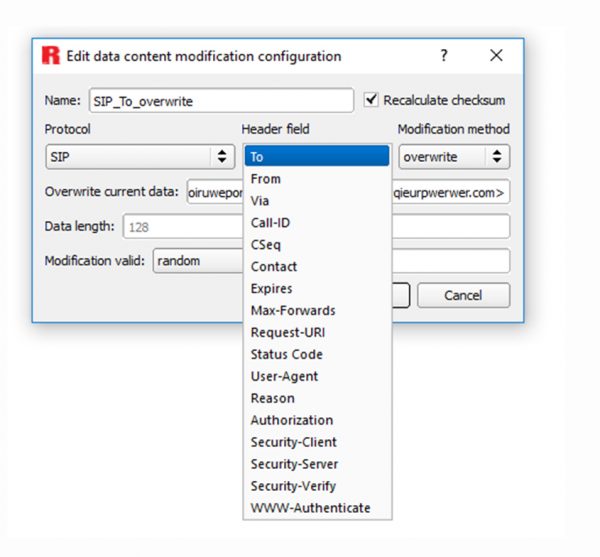
Protocol attributes can be changed in the header fields, as shown in the picture, to replicate any of these possible attacks or several other protocol attacks. This feature enables an easy setup to create the attacks you need to test the system resilience.
SIP and data content modification
Session Initiation Protocol (SIP) is an application-layer control protocol that is widely used for VoIP signaling. It is available for Breeze and Thunder platforms in the release v3.8.6, which is already available, and it will be coming for the Blizzard platform during October 2018.
Data content modification lets a user of the Rude deviation emulator to select a header field in the data and replace, add or remove the contents in the field. The Rude tool will add this change into the live traffic in real time.
We’ve added the SIP protocol based on a request. Thanks to our product structure, we can add new features and protocols flexibly when needed. Contact us to get your requirements in the next releases.